Entra ID User Certificates
Provide certificates for S/MIME and authentication on all your user's devices.
Certificate Automation
Auto-enroll and -renew user certificates from a public or private CA. Auto-revoke changed or removed users.
Management & Self-Service
Role-based basic management of certificates and keys. Recover archived private keys.
Azure Integration
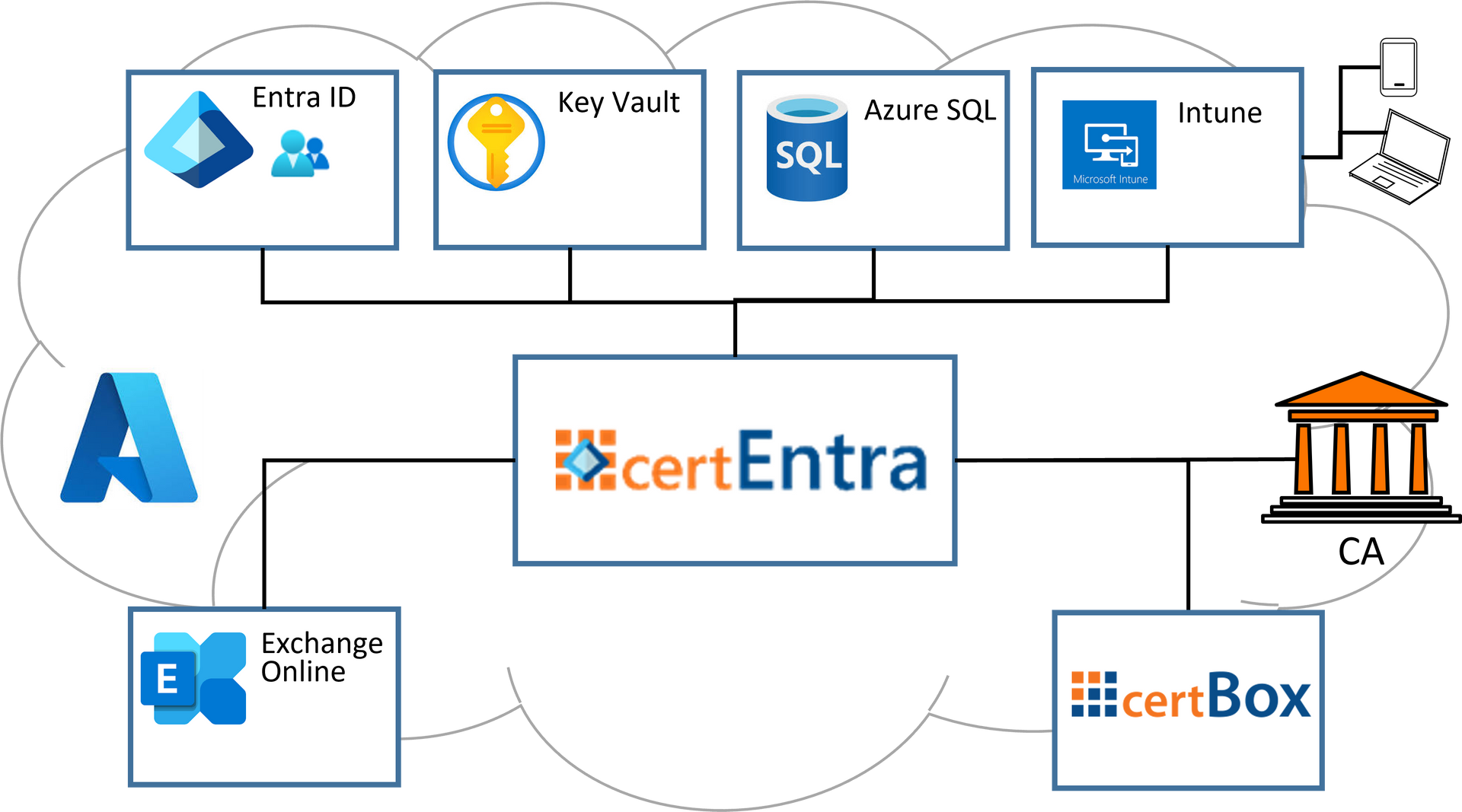
Enroll certificates for Entra ID users to Intune devices and store them in Azure SQL. Use Key Vault for secure key archival.
"Secardeo certEntra enables seamless end-to-end S/MIME encryption and signature and certificate based authentication (CBA) in your Azure infrastructure."
Encrypt and sign e-mails on all devices!
- S/MIME certificates are requested from a public CA.
- Private keys are encrypted and archived in the DB.
- Certificates and private keys are pushed to all devices of a user managed in Intune.
- Certificates are published in GAL or Secardeo certBox so you partners can easily encrypt to you.
- Incoming e-mails are decrypted with your private key.


Certificate based authentication.
- Enable strong user authentication.
- Can be used for 802.1x network access control.
- Option for VPN authentication.
- Conveniently use Microsoft Entra CBA for login.
Use cloud services.
- Entra ID users and groups to request certificates for.
- Intune managed devices to use certificates.
- Azure SQL or other DB to store certificates.
- Key Vault to authenticate and recover private keys.
- Exchange Online for e-mails and publishing certificates.
- Secardeo certBox to publish certificates externally.
- Private or public CA to issue and revoke certificates.

Support major e-mail apps.
- Outlook on Windows
- Native mail apps on iOS and Android.
- MS Outlook for iOS and Android.
- Apple mail on MacOS
How it works
certEntra allows for the central autoenrollment of digital user certificates for Entra ID users in the Azure cloud and the provision of certificates on the devices of the user which are managed in Intune. By this, encryption, signature or authentication certificates can be enrolled. A typical use case is the enrollment of multipurpose S/MIME certificates from a public CA. These certificates can then be used for end-to-end e-mail encryption and signature on all managed devices of the user. Another scenario is the enrollment of user authentication certificates from a private CA like Microsoft ADCS which are needed for certificate based authentication (CBA). These certificates can be used for user authentication by a web server, VPN system, network access control (IEEE 802.1x) or even Entra ID CBA.
certEntra runs on a virtual machine in the customer's Azure cloud or even on-premises and it is therefore under its own full control. A customer owned Azure Key Vault is used for the required credentials and keys. The certificates and archived private keys are stored in a self-hosted or preferably a managed SQL database like Microsoft Azure SQL. The certEntra web app can be accessed by authorized Entra ID users with role based privileges. In order to enroll certificates from a public CA like SwissSign, GlobalSign or Digicert, a corresponding contract for domain validated or organization validated certificates is required and the CA's API credentials will be used by certEntra for the connection.
In certEntra you can configure certificate templates that will serve for your use cases and that link with a certificate product on the CA side. Based on a template and the attached certEntra enrollment group, key pairs are generated for each user and a certificate request is sent to the corresponding CA. The issued certificate together with the encrypted private key is then provisioned to Intune. Intune will then push the certificates and private keys to all configured devices of a user.
The issued certificate is always stored immediately in the database. Private decryption keys are encrypted with Key Recovery Agents (KRA) certificates and then they can be archived in the database. The private KRA keys are used for the later recovery of the private user keys and they can reside on the certEntra host or in the customer's Key Vault. For high security requirements, HSM based Key Vault keys can be used.
S/MIME certificates which are intended for encryption can optionally be published to the Exchange Online GAL or to a Secardeo certBox. The GAL enables encryption between users within an organization. The Secardeo certBox enables internal and external encryption with outside partners who can easily retrieve a user's certificate for encryption.
certEntra also supports the enrollment of certificates for shared mailboxes and the automated delegation and provision to the authorized Entra ID users.
User certificates are automatically renewed before they expire. They are automatically revoked when the user has changed name attributes or has been removed from the enrollment group. Requesting or revoking a certificate can also be performed manually by the certEntra administrator or by the user himself via the user self-service option. Certificate recovery can be performed by the certificate owner or by a user with the role KRA. Customizable notifications can inform the administrator or user about such events.



