certEntra Deployment in Azure Marketplace
I. Purpose of this guide
This guide describes the deployment of the Secardeo certEntra service from the Azure marketplace. It serves as a guideline for planning, installing, configuring and operating certEntra.
As an alternative option, certEntra can also be deployed manually by using a local setup.exe. For further information please contact us.
1. What it does
certEntra allows for the central autoenrollment of digital user certificates in the Azure cloud. Typical use cases are
- end-to-end e-mail encryption using S/MIME certificates from a public CA or
- certificate based authentication (CBA) of the user
Microsoft Entra ID groups control which users the certificates are enrolled for. The certificates are distributed to the user’s devices via Intune.
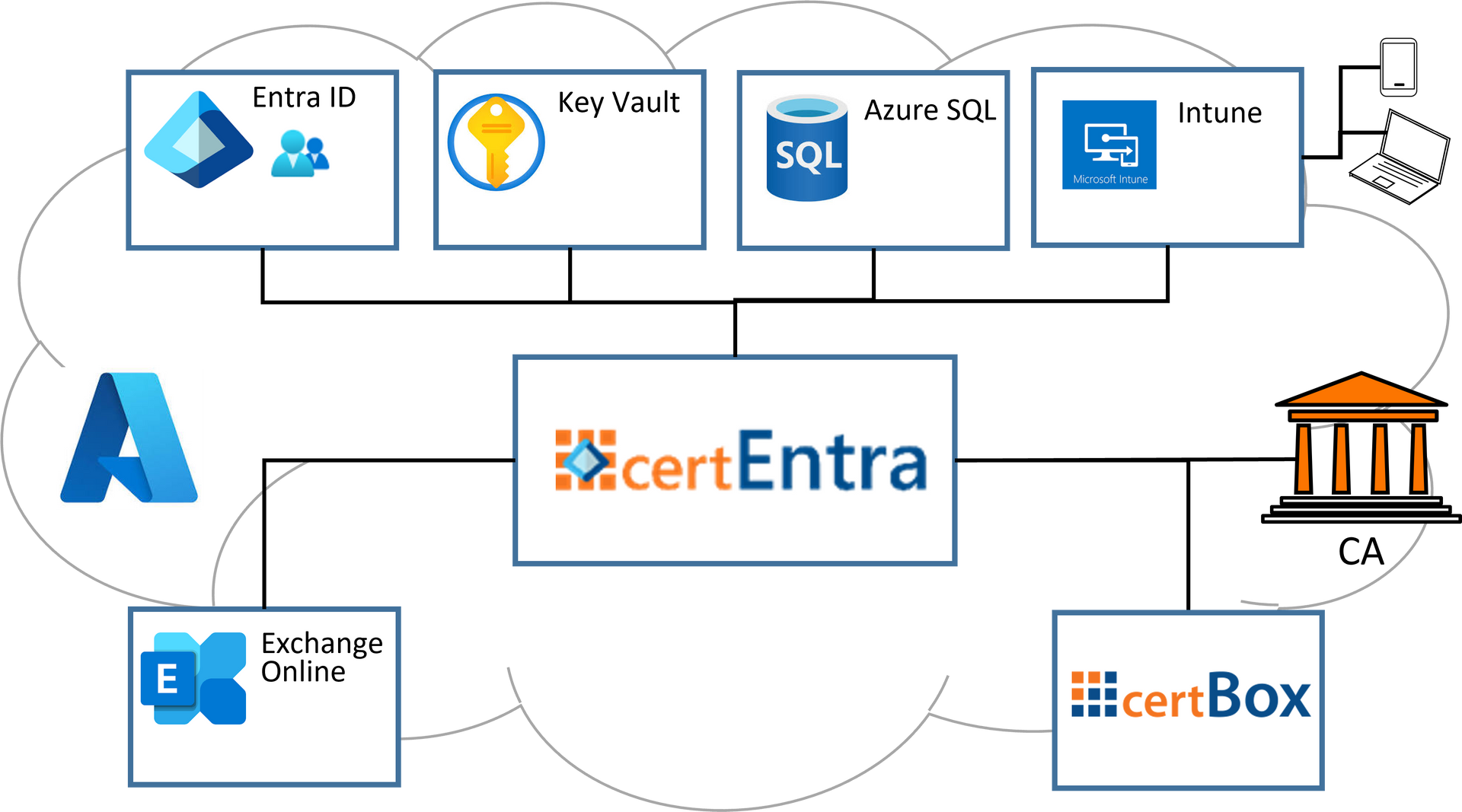
2. How it works
certEntra is installed on a Windows Server VM that is running in Azure. certEntra is using the TOPKI database in Azure SQL, MS SQL or MySQL. To retrieve necessary information from Entra ID, certEntra communicates with your azure tenant. Permissions for this are configured via an Azure app registration. The credentials for the App Registration and optionally private keys are stored in Azure Key Vault. To enable Intune to push the certificates to the users’ devices, an Intune Certificate Connector is required. Certificates can automatically be published in Exchange Online GAL for internal encryption or in the Secardeo certBox for spontaneous encryption with external partners.
II. Prerequisites
1. Backend CA
Currently the following backend CAs are supported:
• DigiCert CertCentral
• D-Trust CMP
• GlobalTrust SOAP
• GlobalSign Atlas
• Sectigo Certificate Manager (SCM) REST
• SwissSign CMC
• Windows CA HTTP
Please make sure that you prepare for the certEntra configuration in a later step
• required API credentials
• certificate products and profiles
2. Database
certEntra supports the following database types:
• Azure SQL
• Azure Database for MySQL
• Microsoft SQL Server 2016 or higher
• MySQL v9 or higher
3. Azure permissions
Global administrator Azure permissions are required during the steps in the deployment guide..
4. Custom domain name (optional)
During deployment, certEntra automatically requests a certificate from Let’s Encrypt for the automatically generated DNS domain name. This domain name can optionally be replaced with a custom domain name later in the configuration, see certEntra manual.
Please make sure you have the necessary rights at your DNS provider to create an A record for your custom domain name.
5. License
certEntra is licensed using Bring-Your-Own-License (BYOL) model. Fill out our contact form to receive a demo licence or purchase a software subscription license.
III. App registration
1. Create app registration

Create an Azure App Registration and configure a client secret for it. Detailed documentation from Microsoft can be found here. The core steps are outlined in the following:
1. Go to your Azure portal and search for “App registrations”
2. Click on “New registration
3. Choose a name, e.g. “certEntra”
4. Choose Accounts in this organizational directory only
5. Click “Register”
2. Add client secret
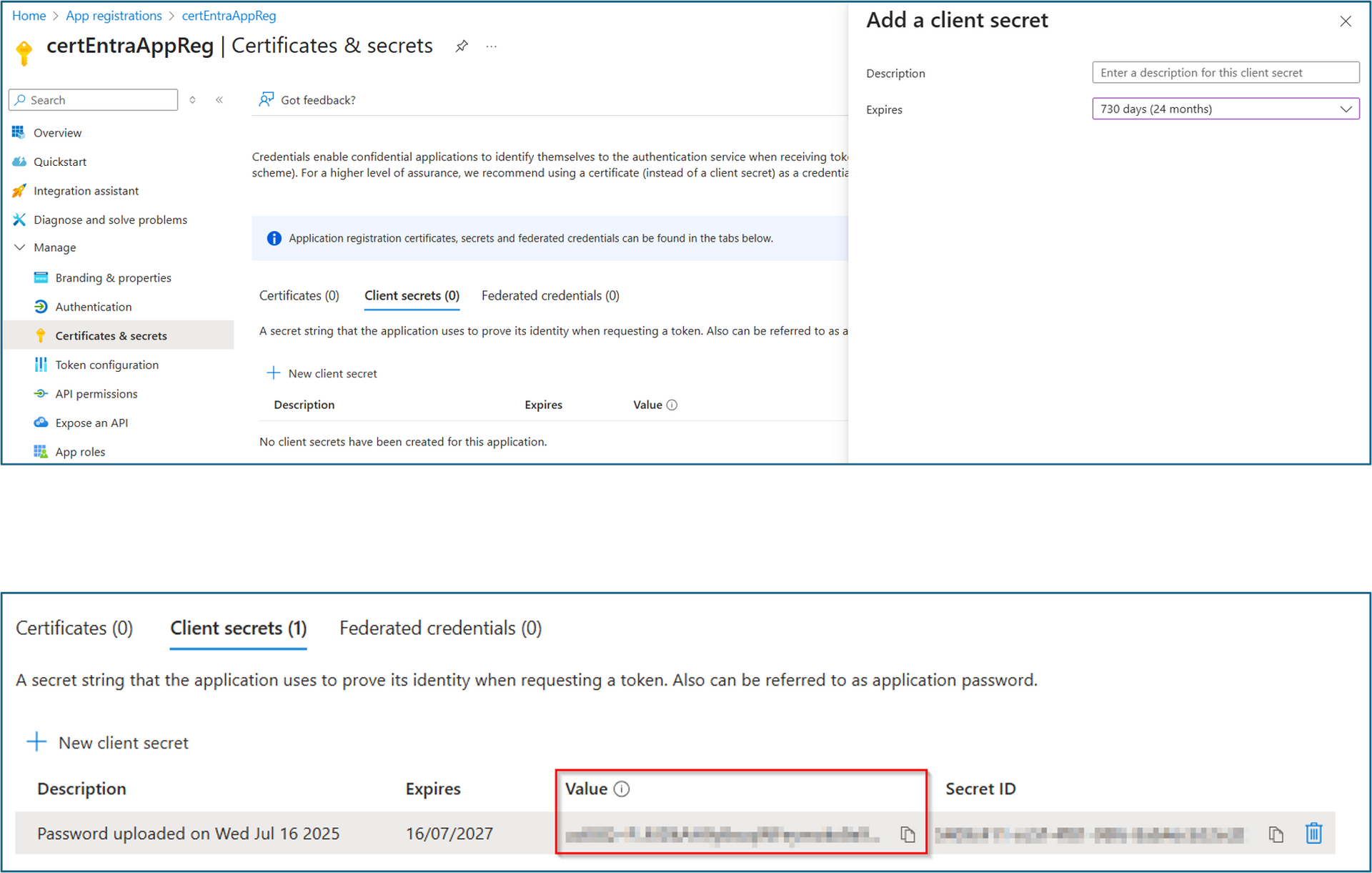
1. On the newly registered app registration under “Certificates & secrets”-“Client secrets” click “New client secret”
2. Give it a name, e.g. “certEntra”. Create a client secret and choose an appropriate expiration (recommended: 24 months)
3. On the “Certificates & secrets” page under “Client secrets” copy the secret string from the “Value” field.
4. Save this secret to a safe place. It won’t be shown again when you leave the page.
5. Save also the Application (client) ID and the Directory (tenant) ID.
3. Add API permissions
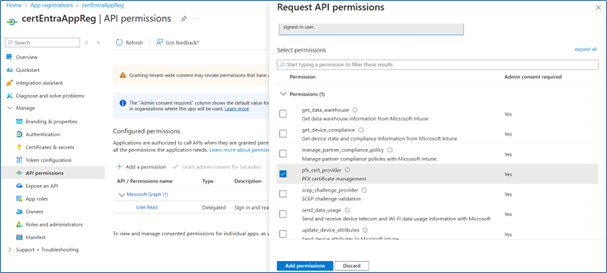
Next configure the permissions that certEntra will get in your Azure Tenant. In your App registration click on “API Permissions” and perform the following steps:
1. Click “Manage“ „API Permissions”
2. Click “Add a permission”
3. Select “Intune”
4. Select “Application permissions”
5. Select “pfx_cert_provider”
6. Click “Add permissions”
6. Select Permissions
1. Click “Add a permission”
2. Select “Microsoft Graph”
3. Select “Application permissions”
4. Select
“Directory”-“Directory.Read.All”,
“Group”-"Group.Read.All”, “GroupMember”-"GroupMember.Read.All”,
“User”-“User.Read.All” (“User.Read” will be delegated),
"DeviceManagementConfiguration"-"DeviceManagementConfiguration.ReadWrite.All"
5. If you want certEntra to send notifications through Exchange Online, you should also add the permission “Mail”-"Mail.Send”.
6. If you want certEntra to Delegate certificates issued to shared Mailboxes, you should also add the permissions
"MailboxSettings”-“MailboxSettings.Read" under “Microsoft Graph” and
“Exchange”-“Exchange.ManageAsApp” under “APIs my organization uses”-“Office 365 Exchange Online”.
7. Click “Add permissions”
7. Grant admin consent

After you’ve added all the permissions: Click “Grant admin consent for [YourTenantName]”. Your permissions should now look like the figure on the left.
8. Add groups claim

To verify the user permissions, certEntra requires the configuration of claims of the app registration in Azure.
You must add groups as an optional claim to your app registration in Azure.
1. Navigate to the created app registration in Azure and go to “Manage” -“Token configuration”.
2. Select “Add groups claim”
3. Select “Security groups” and press “Add”.
If you have more than 200 Entra ID groups, it would be recommended to select the option “Groups assigned to the application” and assign the group to the application in the “Users and Groups” selection from the “Enterprise applications” list (see Manage users and groups assignment to an application - Microsoft Entra ID | Microsoft Learn).
9. Configure Exchange Administrator permissions

This step is only required:
- If certificates for shared mailboxes should be enrolled, or
- If enrolled certificates should be published to the global address list (GAL)
To configure Exchange Administrator permissions:
- In the Azure portal, search and select “Microsoft Entra roles and administrators”. Under “Administrative roles”, search and select “Exchange Administrator”.
- Click “Add assignment” and select the app registration. Click “Add”.
IV. Configure role groups
1. Administrator group
To create the administrator group that is privileged to administrate and configure certEntra:
1. Go to your Azure portal, search for “Entra ID” and click on “Groups”
2. Click “New group”
3. Select “Group type” Security, give the group a “Group name” and optionally a “Group description”
4. Select the “Owners” and the “Members” of the group
5. Click “Create”
6. Go to “All groups” and copy the “Object Id” of the group created. It is required during Marketplace deployment.
2. KRA group
To configure the key recovery agent group for key recovery operations:
1. Click “New group”
2. Select “Group type” Security, give the group a “Group name” and optionally a “Group description”
3. Select the “Owners” and the “Members” of the group
4. Click “Create”
5. Go to “All groups” and copy the “Object Id” of the group created. It is required during Marketplace deployment.
3. Enrollment groups
Each certificate template configured in certEntra requires a certificate enrollment group in Entra ID that contains the users certEntra will issue certificates for. To create one of these groups in Entra ID do the following:
1. Click “New group”
2. Select “Group type” Security, give the group a “Group name” and optionally a “Group description”
3. Select the “Owners” and the “Members” of the group
4. Click “Create”
Note:
certEntra does not support certificate issuance for nested enrollment groups.
V. Marketplace deployment
After looking up certEntra on the Azure marketplace you can choose to “Create” the certEntra plan.
1. Basics

The first page allows you to make basic configurations:
1. Choose your subscription
2. Choose your resource group or create a new one
3. Choose your region
4. Choose your virtual machine name
5. Click “Next”
2. Virtual machine settings
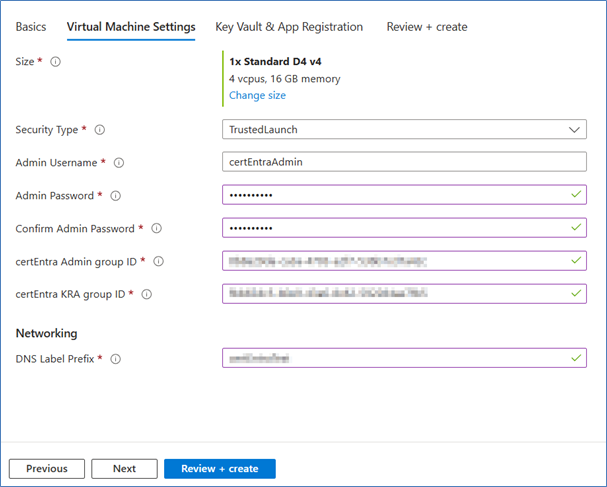
certEntra is always deployed as a “2022 Datacenter Azure Edition” VM.
1. Choose the size of your VM (based on default VM-Sizes in Azure, see Appendix A) for more info)
2. Choose a name for your admin user on the VM
3. Choose a password for this user
4. Enter the certEntra Administrators groups “Object Id”
5. Enter the certEntra KRA groups “Object Id”
6. Choose a DNS Label prefix. This must be lowercase
7. Click “Next”
3. Key vault & app registration
In the Key vault & app registration page do the following:
1. Choose your desired key vault SKU. Select “Standard” for a non-HSM key vault. For an HSM key vault, select “Premium”
2. Choose a globally unique name for your key vault. Ensure that the name does not match the name of your virtual machine
3. Enter the Client ID of your app registration created before
4. Enter the Client Secret of your app registration icreated before
5. Enter your Tenant ID
6. Click “Next”
4. Review + create
After entering the required values, review your settings. If they are correct you can proceed with creating your certEntra-VM by clicking “create”. Your VM will then be deployed (~ 15 min).
Once the deployment is complete, click “Go to Resource” to open your newly created resource group. You can also monitor the deployment progress from the Azure portal under the selected resource group.
In the deployment output, you’ll find the fully qualified domain name (FQDN) where certEntra is accessible.
If the deployment completed successfully, you can access the application at “https://
/certEntra”
VI. Configure authentication
1. Entra ID Authentication
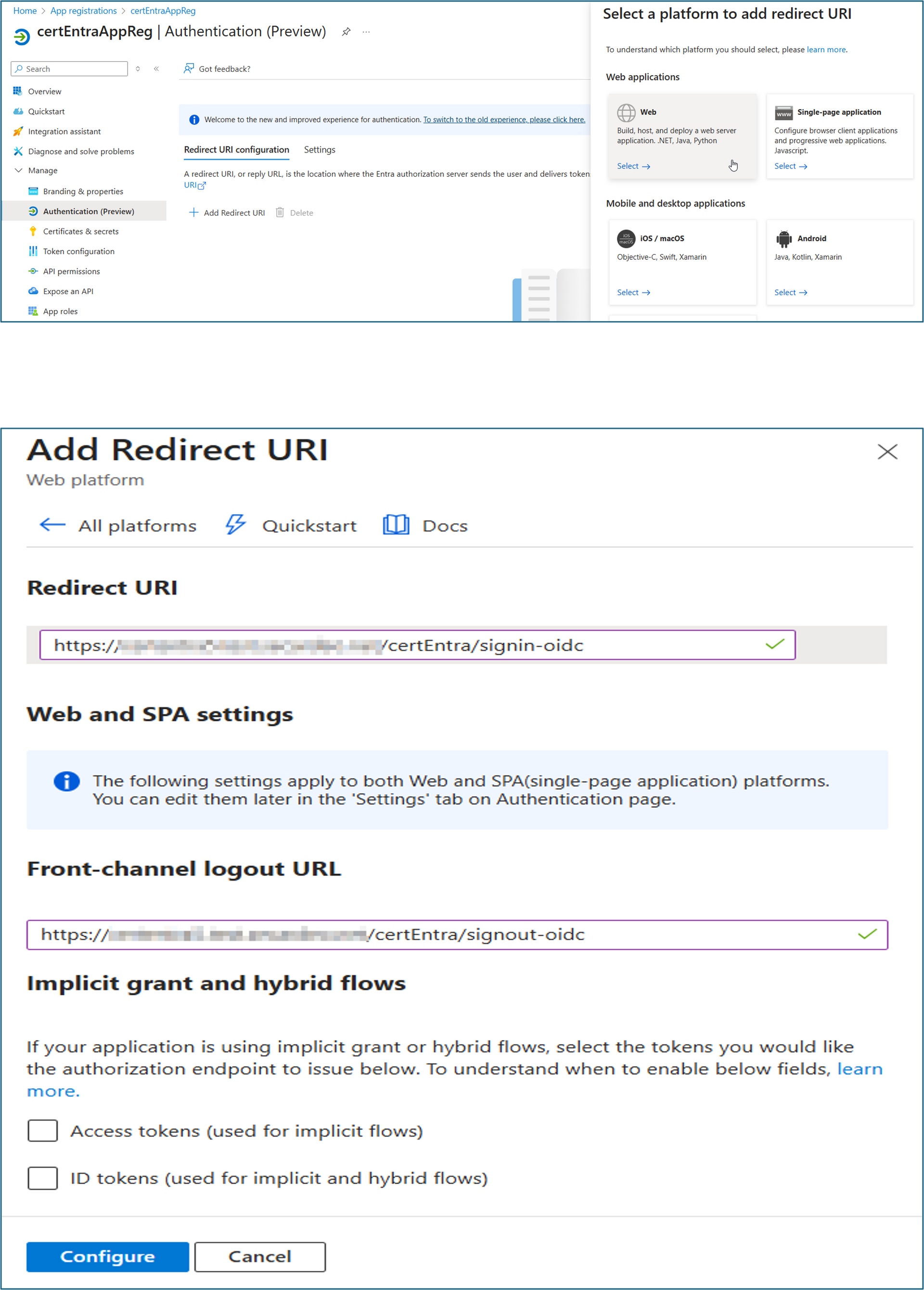
Next enable Entra ID Authentication for certEntra.
1. In the Azure portal, open the configuration of your app registration and click on “Manage-Authentication”
2. Click “Add Redirect URI”
3. Choose “Web”
4. Enter https://
/certEntra/signin-oidc (“ ” is the domain name of your virtual machine which you configured above) at “Redirect URI” 5. Enter https://"FQDN"/certEntra/signout-oidc (“FQDN” is the domain name of your virtual machine which you configured above) at “Front-channel logout URL”
6. Click “Configure”
2. RDP access (optional)
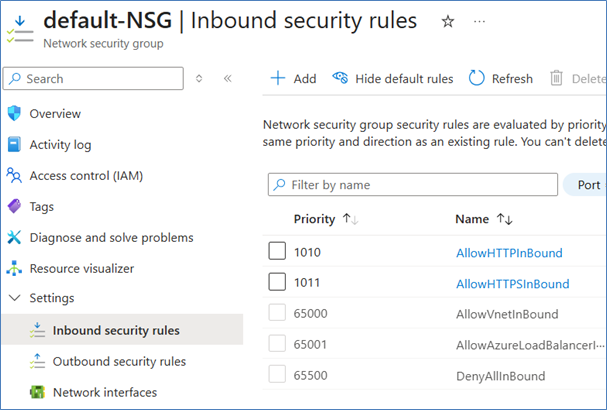
Access via RDP to the virtual machine is disabled by default. However, it may be required in these cases:
• During Intune certificate connector configuration
• To configure an individual TLS certificate
RDP can be enabled by either configuring Azure Bastion or modifying the Network Security Group (NSG) to allow the standard RDP port (3389).
Azure Bastion is a fully managed service that provides secure RDP connectivity to virtual machines directly through the Azure Portal, without exposing those VMs to the public internet.
1. To open the RDP port 3389 by configuring NSG, go to the created resource group in the Azure portal
2. Click on “default-NSG” and select "Settings” “Inbound security rules”
3. Then click “Add” and configure the security rule for the “Service” “RDP”
4. Configure the source and port settings according to your individual network requirements.
5. Press “Add”
VII. Configure Intune certificate connector
In order to distribute private keys, the certificate connector for Microsoft Intune for imported PKCS is needed. If you already have an existing “PKCS Import” Intune certificate connector, you can reuse it for certEntra . If not, a new connector can be installed on the certEntra machine or on any other machine (see
Use imported PFX certificates in Microsoft Intune | Microsoft Learn).
1. Check if certificate connector exists
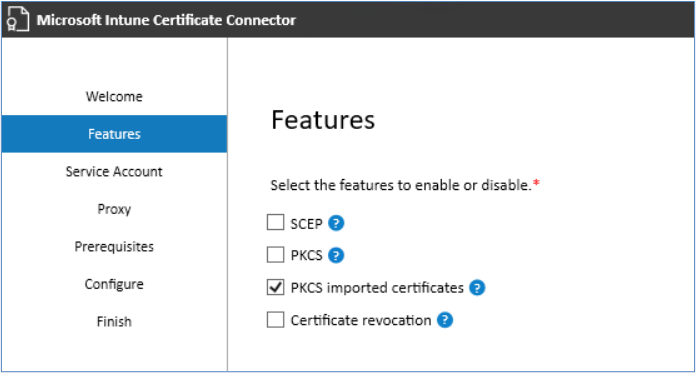
To verify, if you already have a “PKCS Import” connector:
1. Login in the “Microsoft Intune Admin center”
2. Go to “Tenant Administration” -> “Connectors and tokens” -> “Certificate connectors” All connectors are displayed, but the Intune portal does not show the connector type.
3. In order to find out the connector type, you but must login on the machine where the connector is installed.
4. On the machine open the “Certificate Connector for Microsoft Intune”
5. Click on “Next”
6. Check, if the “PKCS imported certificates” is selected
If you have found an existing PKCS connector, you will have to configure the corresponding KSP key in certEntra. This is described in the certEntra manual.
2. Create certificate connector

If you don’t have an “PKCS Import” Intune certificate connector yet, please create it on the certEntra machine. You must follow these steps:
1. Login on the certEntra machine. For this, RDP access must be enabled.
2. Run the provided “CreateKSPkey.bat” File as Local Administrator. It can be found on your certEntra machine in the Tool folder (C:\Program Files\Secardeo\certEntra\Tools\IntuneKSPgenerator).
3. Open the installed “Certificate Connector for Microsoft Intune Setup” and click 3. “Configure Now”
4. Configure the connector and follow the instructions. Select these options:
a. “Features”: “PKCS imported certificate”
b. “Service Account”: “System Account”
c. “Proxy”: configure no proxy
d. “Azure AD Sign In”: “Public Commercial Cloud”. Then login as the global administrator.
5. Click “Next” and “Exit” to finish the configuration
To see if the Connector has been added successfully you can perform the steps for "Check if certificate connector exists"
A full guide can be found here.
VIII. Optional steps
1. Create Azure SQL server
If you don’t have an already existing database server yet, we suggest to create one in your Azure Tenant.
1. In the Azure portal, search for “SQL servers” in the top search bar
2. Click “Create” and enter a globally unique server name, such as “topki-sqlserver”
3. Under “Authentication method”, choose the option that fits your setup:
a. “Use Microsoft Entra-only authentication”
b. “Use both SQL and Microsoft Entra authentication”, or
c. “Use SQL authentication”
4. Configure the “Microsoft Entra admin” and/or “Instance admin login” depending on the selection of the “Authentication method”.
a. If you want to use SQL authentication, you must create a new user with a password that will be set as the administrator of the database. Please remember the credentials of the “Instance admin login” to create an additional database user for certEntra. This is required in the database configuration step in the certEntra manual.
b. If you choose “Microsoft Entra authentication”, you must configure an Entra ID account that will be set as the administrator of the database server. If you want to configure Entra authentication as a login option, you must be able to login as the “Microsoft Entra admin” at the database server.
5. In the “Networking” tab, toggle “Allow Azure services and resources to access this server” to “Yes”
6. In the “Security” tab, don’t any “Configure Identities”
7. Configure the rest of the attributes according to your needs or leave them with the default
8. Click “Review + Create” and “Create”
9. After the database server is deployed, click on the database server. Go to “Security”- “Networking” and configure the networking. The database server must be accessible from the certEntra machine.
2. Create Azure Database for MySQL server
As ana alternative to Azure SQL you can create an Azure Database for MySQL server:
1. Go to your Azure portal and search for “Azure Database for MySQL servers”
2. Click “Create” and enter a server name, e.g. “TOPKI”
3. For “Authentication method”, choose at least “Use SQL authentication”. certEntra does not support Microsoft Entra authentication for MySQL databases.
4. Configure a “Server admin login” and password. Please remember the credentials. They are required in the database configuration step in the certEntra manual.
5. In the “Networking” tab toggle “Allow Azure services and resources to access this server” to “Yes”
6. Configure the rest of the attributes according to your needs or leave the with the default
3. Configure Entra authentication for Azure SQL
certEntra can connect to Azure SQL databases using Entra Authentication via the app registration. For this, the app registration user has to be created with proper permissions on the database server. For more information, please refer to the Microsoft documentation.
1. Go to the Azure portal to “Enterprise applications” → “All applications”
2. Select the app registration configured previously
3. Copy the “Object ID”
4. Go in the Azure portal to “Azure SQL” and select the Azure SQL database server to get the “Microsoft Entra admin” account
5. Login to the database server as the “Microsoft Entra admin”. You can use “Microsoft SQL Server Management Studio”
6. Create the external user for the app registration on the database server based on the “Object ID”:
CREATE USER [name-of-app-registration]
FROM EXTERNAL PROVIDER
WITH OBJECT_ID = 'object-id';
GO
ALTER ROLE dbmanager ADD MEMBER [name-of-app-registration];
ALTER ROLE loginmanager ADD MEMBER [name-of-app-registration];
Note: The “[“ and “]” symbols are required and must not be removed.
7. You can validate that the user was successfully created:
SELECT name, type_desc, authentication_type_desc
FROM sys.database_principals
WHERE type IN ('E', 'X')
AND name = 'name-of-app-registration';
4. Configure individual TLS certificate
certEntra automatically requests a certificate from Let’s Encrypt. If you wish to request a certificate from an individual CA, you can request this manually by logging onto the virtual machine via RDP and using the installed ACME client.
After logging onto the machine via RDP, the TLS certificate can be configured:
1. Request and install a TLS certificate with the private key in the local machine certificate store (certlm.msc. The certificate must contain the FQDN of the machine in the subject alternative name extension.
2. Open the IIS and navigate to “Sites” “Default Web Site”
3. Select the option “Bindings” in the menu on the right
4. Add a binding on port 443 in the IIS using the installed certificate. The certificate should be available here, if it is installed in the local machine certificate store
IX. Proceed with certEntra configuration
Now, the deployment of certEntra is completed and you can proceed with the certEntra configuration. For this, open your web browser and enter the URL https://<FQDN>/certEntra.
The configuration of certEntra is described in the certEntra manual.
X. Contact
Secardeo GmbH
Hohenadlstr.4
D-85737 Ismaning
Germany
E-Mail: support@secardeo.com
Phone: +49 89 18 93 58 9-8


